APTnotes: histórico de APTs
APTnotes es un repositorio de varios documentos y notas relacionadas a APTs, disponibles públicamente y ordenados por año. Algunos de estos reportes inckuso contienen hashes de muestras de malware para analizar en un entorno de laboratorio.
La idea del proyecto es tener una copia de cada documento publicado y que cualquiera pueda contribuir y agregar documentos.
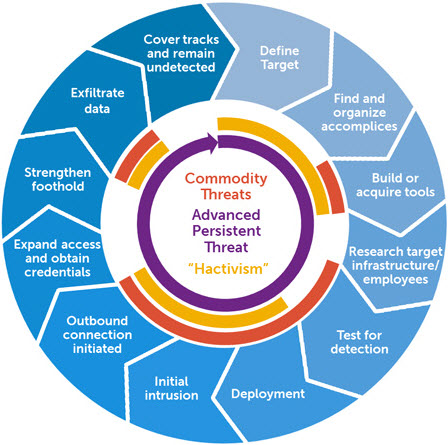
La idea del proyecto es tener una copia de cada documento publicado y que cualquiera pueda contribuir y agregar documentos.
2006

2008
- Aug 10 - Russian Invasion of Georgia Russian Cyberwar on Georgia
- Oct 02 - How China will use cyber warfare to leapfrog in military competitiveness
- Nov 04 - China's Electronic Long-Range Reconnaissance
- Nov 19 - Agent.BTZ
2009
- Jan 18 - Impact of Alleged Russian Cyber Attacks
- Mar 29 - Tracking GhostNet
2010
- Jan 12 - Operation Aurora
- Jan 13 - The Command Structure of the Aurora Botnet - Damballa
- Jan 20 - McAfee Labs: Combating Aurora
- Jan 27 - Operation Aurora Detect, Diagnose, Respond
- Jan ?? - Case Study: Operation Aurora - Triumfant
- Feb 24 - How Can I Tell if I Was Infected By Aurora? (IOCs)
- Mar 14 - In-depth Analysis of Hydraq
- Apr 06 - Shadows in the cloud: Investigating Cyber Espionage 2.0
- Sep 03 - The "MSUpdater" Trojan And Ongoing Targeted Attacks
- Sep 30 - W32.Stuxnet Dossier
- Dec 09 - The Stuxnet Computer Worm: Harbinger of an Emerging Warfare Capability
2011
- Feb 10 - Global Energy Cyberattacks: Night Dragon
- Feb 18 - Night Dragon Specific Protection Measures for Consideration
- Apr 20 - Stuxnet Under the Microscope
- Aug ?? - Shady RAT
- Aug 04 - Operation Shady RAT
- Aug 02 - Operation Shady rat : Vanity
- Aug 03 - HTran and the Advanced Persistent Threat
- Sep 09 - The RSA Hack
- Sep 11 - SK Hack by an Advanced Persistent Threat
- Sep 22 - The "LURID" Downloader
- Oct 12 - Alleged APT Intrusion Set: "1.php" Group
- Oct 26 - Duqu Trojan Questions and Answers
- Oct 31 - The Nitro Attacks: Stealing Secrets from the Chemical Industry
2012
- Jan 03 - The HeartBeat APT
- Feb 03 - Command and Control in the Fifth Domain
- Feb 29 - The Sin Digoo Affair
- Mar 12 - Crouching Tiger, Hidden Dragon, Stolen Data
- Mar 13 - Reversing DarkComet RAT's crypto
- Mar 26 - Luckycat Redux
- Apr 10 - Anatomy of a Gh0st RAT
- Apr 16 - OSX.SabPub & Confirmed Mac APT attacks
- May 18 - Analysis of Flamer C&C Server
- May 22 - IXESHEA An APT Campaign
- May 31 - sKyWIper (Flame/Flamer)
- Jul 10 - Advanced Social Engineering for the Distribution of LURK Malware
- Jul 11 - Wired article on DarkComet creator
- Jul 27 - The Madi Campaign
- Aug 09 - Gauss: Abnormal Distribution
- Sep 06 - The Elderwood Project
- Sep 07 - IEXPLORE RAT
- Sep 12 - The VOHO Campaign: An in depth analysis
- Sep 18 - The Mirage Campaign
- Oct 08 - Matasano notes on DarkComet, Bandook, CyberGate and Xtreme RAT
- Oct 27 - Trojan.Taidoor: Targeting Think Tanks
- Nov 01 - RECOVERING FROM SHAMOON
- Nov 03 - Systematic cyber attacks against Israeli and Palestinian targets going on for a year
2013
- Jan 18 - Ooperation Red October
- Feb 12 - Targeted cyber attacks: examples and challenges ahead
- Feb 13 - Operation SnowMan: DeputyDog Actor Compromises US Veterans of Foreign Wars Website
- Feb 18 - Mandiant APT1 Report
- Feb 22 - Comment Crew: Indicators of Compromise
- Feb 26 - Stuxnet 0.5: The Missing Link
- Feb 27 - The MiniDuke Mystery: PDF 0-day Government Spy Assembler 0x29A Micro Backdoor
- Feb 27 - Miniduke: Indicators v1
- Mar 13 - You Only Click Twice: FinFisher’s Global Proliferation
- Mar 17 - Safe: A Targeted Threat
- Mar 20 - Dissecting Operation Troy
- Mar 20 - The TeamSpy Crew Attacks
- Mar 21 - Darkseoul/Jokra Analysis And Recovery
- Mar 27 - APT1: technical backstage (Terminator/Fakem RAT)
- Apr 01 - Trojan.APT.BaneChant
- Apr 13 - "Winnti" More than just a game
- Apr 24 - Operation Hangover
- May ?? - Operation Hangover
- Jun ?? - The Chinese Malware Complexes: The Maudi Surveillance Operation
- Jun 01 - Crude Faux: An analysis of cyber conflict within the oil & gas industries
- Jun 04 - The NetTraveller (aka 'Travnet')
- Jun 07 - KeyBoy, Targeted Attacks against Vietnam and India
- Jun 18 - Trojan.APT.Seinup Hitting ASEAN
- Jun 21 - A Call to Harm: New Malware Attacks Target the Syrian Opposition
- Jun 28 - njRAT Uncovered
- Jul 09 - Dark Seoul Cyber Attack: Could it be worse?
- Jul 15 - PlugX revisited: "Smoaler"
- Jul 31 - Secrets of the Comfoo Masters
- Jul 31 - Blackhat: In-Depth Analysis of Escalated APT Attacks (Lstudio,Elirks), video
- Aug ?? - Operation Hangover - Unveiling an Indian Cyberattack Infrastructure
- Aug ?? - APT Attacks on Indian Cyber Space
- Aug 02 - Where There is Smoke, There is Fire: South Asian Cyber Espionage Heats Up
- Aug 02 - Surtr: Malware Family Targeting the Tibetan Community
- Aug 19 - ByeBye Shell and the targeting of Pakistan
- Aug 21 - POISON IVY: Assessing Damage and Extracting Intelligence
- Aug 23 - Operation Molerats: Middle East Cyber Attacks Using Poison Ivy
- Sep ?? - Feature: EvilGrab Campaign Targets Diplomatic Agencies
- Sep 11 - The "Kimsuky" Operation
- Sep 13 - Operation DeputyDog: Zero-Day (CVE-2013-3893) Attack Against Japanese Targets
- Sep 17 - Hidden Lynx - Professional Hackers for Hire
- Sep 25 - The 'ICEFROG' APT: A Tale of cloak and three daggers
- Sep 30 - World War C: State of affairs in the APT world
- Oct 24 - Terminator RAT or FakeM RAT
- Nov 10 - Operation Ephemeral Hydra: IE Zero-Day Linked to DeputyDog Uses Diskless Method
- Nov 11 - Supply Chain Analysis
- Dev 02 - njRAT, The Saga Continues
- Dec 11 - Operation "Ke3chang"
- Dec 20 - ETSO APT Attacks Analysis
- ??? ?? - Deep Panda
- ??? ?? - Detecting and Defeating the China Chopper Web Shell
2014
- Jan 06 - PlugX: some uncovered points
- Jan 13 - Targeted attacks against the Energy Sector
- Jan 14 - The Icefog APT Hits US Targets With Java Backdoor
- Jan 15 - “New'CDTO:'A'Sneakernet'Trojan'Solution
- Jan 21 - Shell_Crew (Deep Panda)
- Jan 31 - Intruder File Report- Sneakernet Trojan
- Feb 11 - Unveiling "Careto" - The Masked APT
- Feb 13 - Operation SnowMan: DeputyDog Actor Compromises US Veterans of Foreign Wars Website
- Feb 19 - The Monju Incident
- Feb 19 - XtremeRAT: Nuisance or Threat?
- Feb 20 - Operation GreedyWonk: Multiple Economic and Foreign Policy Sites Compromised, Serving Up Flash Zero-Day Exploit
- Feb 20 - Mo' Shells Mo' Problems - Deep Panda Web Shells
- Feb 23 - Gathering in the Middle East, Operation STTEAM
- Feb 28 - Uroburos: Highly complex espionage software with Russian roots
- Mar 06 - The Siesta Campaign
- Mar 07 - Snake Campaign & Cyber Espionage Toolkit
- Mar 08 - Russian spyware Turla
- Apr 26 - CVE-2014-1776: Operation Clandestine Fox
- May 13 - Operation Saffron Rose (aka Flying Kitten)
- May 13 - CrowdStrike's report on Flying Kitten
- May 21 - RAT in jar: A phishing campaign using Unrecom
- Jun 06 - Illuminating The Etumbot APT Backdoor (APT12)
- Jun 09 - Putter Panda
- Jun 30 - Dragonfly: Cyberespionage Attacks Against Energy Suppliers
- Jun 10 - Anatomy of the Attack: Zombie Zero
- Jul 07 - Deep Pandas
- Jul 11 - Pitty Tiger
- Jul 20 - Sayad (Flying Kitten) Analysis & IOCs
- Jul 31 - Energetic Bear/Crouching Yeti
- Jul 31 - Energetic Bear/Crouching Yeti Appendix
- Aug 04 - Sidewinder Targeted Attack Against Android
- Aug 05 - Operation Arachnophobia
- Aug 06 - Operation Poisoned Hurricane
- Aug 07 - The Epic Turla Operation Appendix
- Aug 12 - New York Times Attackers Evolve Quickly (Aumlib/Ixeshe/APT12)
- Aug 13 - A Look at Targeted Attacks Through the Lense of an NGO
- Aug 18 - The Syrian Malware House of Cards
- Aug 20 - El Machete
- Aug 25 - Vietnam APT Campaign
- Aug 27 - NetTraveler APT Gets a Makeover for 10th Birthday
- Aug 27 - North Korea’s cyber threat landscape
- Aug 28 - Scanbox: A Reconnaissance Framework Used with Watering Hole Attacks
- Aug 29 - Syrian Malware Team Uses BlackWorm for Attacks
- Sep 03 - Darwin’s Favorite APT Group (APT12)
- Sep 04 - Forced to Adapt: XSLCmd Backdoor Now on OS X
- Sep 08 - Targeted Threat Index: Characterizingand Quantifying Politically-MotivatedTargeted Malware video
- Sep 08 - When Governments Hack Opponents: A Look at Actors and Technology video
- Sep 10 - Operation Quantum Entanglement
- Sep 17 - Chinese intrusions into key defense contractors
- Sep 18 - COSMICDUKE: Cosmu with a twist of MiniDuke
- Sep 19 - Watering Hole Attacks using Poison Ivy by "th3bug" group
- Sep 23 - Ukraine and Poland Targeted by BlackEnergy (video)
- Sep 26 - Aided Frame, Aided Direction (Sunshop Digital Quartermaster)
- Sep 26 - BlackEnergy & Quedagh
- Oct 03 - New indicators for APT group Nitro
- Oct 09 - Democracy in Hong Kong Under Attack
- Oct 14 - ZoxPNG Preliminary Analysis
- Oct 14 - Hikit Preliminary Analysis
- Oct 14 - Derusbi Preliminary Analysis
- Oct 14 - Group 72 (Axiom)
- Oct 14 - Sandworm - CVE-2104-4114
- Oct 20 - OrcaRAT - A whale of a tale
- Oct 22 - Operation Pawn Storm: The Red in SEDNIT
- Oct 22 - Sofacy Phishing by PWC
- Oct 23 - Modified Tor Binaries
- Oct 24 - LeoUncia and OrcaRat
- Oct 27 - Full Disclosure of Havex Trojans - ICS Havex backdoors
- Oct 27 - ScanBox framework – who’s affected, and who’s using it?
- Oct 28 - APT28 - A Window Into Russia's Cyber Espionage Operations
- Oct 28 - Group 72, Opening the ZxShell
- Oct 30 - The Rotten Tomato Campaign
- Oct 31 - Operation TooHash
- Nov 03 - New observations on BlackEnergy2 APT activity
- Nov 03 - Operation Poisoned Handover: Unveiling Ties Between APT Activity in Hong Kong’s Pro-Democracy Movement
- Nov 10 - The Darkhotel APT - A Story of Unusual Hospitality
- Nov 11 - The Uroburos case- Agent.BTZ’s successor, ComRAT
- Nov 12 - Korplug military targeted attacks: Afghanistan & Tajikistan
- Nov 13 - Operation CloudyOmega: Ichitaro 0-day targeting Japan
- Nov 14 - OnionDuke: APT Attacks Via the Tor Network
- Nov 14 - Roaming Tiger (Slides)
- Nov 21 - Operation Double Tap | IOCs
- Nov 23 - Symantec's report on Regin
- Nov 24 - Kaspersky's report on The Regin Platform
- Nov 24 - TheIntercept's report on The Regin Platform
- Nov 30 - FIN4: Stealing Insider Information for an Advantage in Stock Trading?
- Dec 02 - Operation Cleaver | IOCs
- Dec 03 - Operation Cleaver: The Notepad Files
- Dec 08 - The 'Penquin' Turla
- Dec 09 - The Inception Framework
- Dec 10 - Cloud Atlas: RedOctober APT
- Dec 10 - W32/Regin, Stage #1
- Dec 10 - W64/Regin, Stage #1
- Dec 12 - Vinself now with steganography
- Dec 12 - Bots, Machines, and the Matrix
- Dec 17 - Wiper Malware – A Detection Deep Dive
- Dec 18 - Malware Attack Targeting Syrian ISIS Critics
- Dec 19 - TA14-353A: Targeted Destructive Malware (wiper)




0 Comments:
Publicar un comentario
Gracias por dejar un comentario en Segu-Info.
Gracias por comentar!